📝 Blog Summary
PBX migration is not a basic hardware swap. It’s an end-to-end modernization of your communication backbone. This blog offers service providers the expert checklist to standardize every step, from securing sensitive call data during transfer to leveraging cloud-native architecture for future scalability.
For years, that hefty Private Branch Exchange (PBX) has been a reliable (even if rigid) workhorse. But today, with PSTN lines being phased out, customer demand for instant communication soaring, and AI quickly evolving what’s possible, the legacy PBX has become a liability. It’s a barrier to growth, incapable of supporting the hybrid workforce or essential AI automation.
The transition to a scalable, cloud-native VoIP ecosystem is no longer optional.
For service providers, this process is exponentially harder: you must execute a standardized, zero-downtime PBX migration plan across dozens of unique client environments while strictly protecting sensitive data. This is not a project for an IT generalist; it’s an end-to-end digital communication transformation.
This checklist provides the expert blueprint for a successful enterprise PBX migration solution, ensuring you move beyond physical hardware toward a resilient, scalable, and future-ready communications architecture.
How to Assess and Standardize Client Risk? (Pre-Migration)
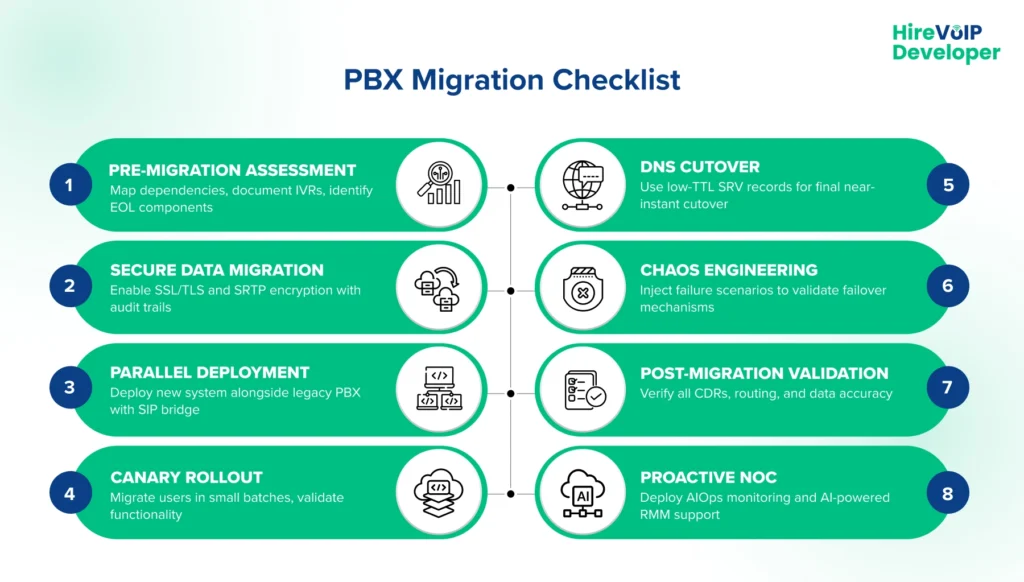
The first step in any successful PBX migration plan is a surgical assessment to standardize risk and dependencies across multiple environments. Basically, it answers what pre-migration assessments should be done to avoid failures.
This assessment dictates whether you can execute a simple “Lift-and-Shift” or if the system requires comprehensive re-platforming.
| Assessment Factor | Description | Mitigation Strategy |
|---|---|---|
| Complexity & Size | Volume of data, number of extensions, and intricacy of call flows (IVRs). | Determine timeline and resource allocation. High complexity mandates re-platforming to a multi-threaded core (e.g., FreeSWITCH). |
| Dependencies Map | Mapping every existing integration (CRM webhooks, fax services, door access, and custom scripting logic). | Crucial for creating accurate rollback plans and ensuring feature parity post-cutover. |
| Technical Debt | Identifying EOL components (e.g., outdated PHP or MariaDB versions) that will no longer receive security patches. | Mandate platform upgrade or re-platforming to a current architecture to eliminate cybersecurity risk exposure. |
Pre-Migration Documentation
Mitigating future risk depends on meticulous documentation. That makes it important to be clear on what data you should capture before shutting down the legacy PBX.
Before decommissioning the legacy PBX, providers must capture:
- Complete Dependency Map: Archive the entire inventory of all external APIs, SIP trunk details, and application integrations.
- Final Call Flow Snapshot: Document the exact configuration of all IVRs, hunt groups, and call routing logic.
- Archive of Data: Archive historical CDR and billing data, along with the final system configuration file and any custom scripts, ensuring compliance for regulatory periods.
Avoid PBX Bottlenecks as 5G Adoption Accelerates
How to Ensure Secure Data Migration During PBX Migration?
Security and performance are intrinsically linked. So, the next step is figuring out how you can ensure a secure migration without exposing sensitive call data of your clients.
Modernizing Infrastructure for Scale and Resilience
Legacy systems are often monolithic, relying on single-threaded architectures that limit concurrent call capacity. Modernization requires a shift to robust, multi-tenant cloud architecture for a secure migration:
- Server Architecture: Migrate from single-system arrangements to scalable, multi-threaded VoIP ecosystems (e.g., FreeSWITCH) that can handle significantly higher concurrent call volume (often 4–10 times the capacity of older systems).
- Cloud Infrastructure: Transition to centralized service lifecycle management for inherent reliability, geo-redundancy, and security.
- Multi-Tenancy: The target must support domain-based multi-tenancy (like FusionPBX), allowing you to securely manage thousands of clients with isolated data from a single, scalable infrastructure instance.
Data Security and Compliance During Transfer
You need to take care of some simple, but crucial things to ensure a secure data transfer during PBX migration:
- Encryption Mandate: Ensure all data in transit (CDRs, voicemail audio files, configuration data) is protected. This requires mandatory encryption using current SSL/TLS and SRTP standards.
- Compliance Audit Trails: Create robust audit trails that track all authentication and provisioning decisions during the transition, providing essential compliance documentation for regulations like HIPAA. Secure access controls must be established for CDRs and voicemail data.
Zero-Downtime Execution of PBX Migration
So, how do you standardize PBX migration across multiple client environments without causing downtime?
The key is a phased approach that isolates risk and utilizes intelligent routing.
- Parallel Deployment & Bridge: Deploy the new cloud-native environment (e.g., FreeSWITCH) alongside the existing legacy PBX. Establish a secure SIP trunk connection (interoperability bridge) between the old and new systems.
- Canary Rollout (Phased Migration): Migrate low-risk users or departments in small batches. Calls between legacy and new users route seamlessly across the SIP bridge, validating functionality under real load.
- Final Cutover via DNS: To minimize the final downtime window, utilize low-TTL (Time-to-Live) SIP SRV records. Changing the DNS record automatically redirects all endpoints to the new system, achieving a near-instant cutover that is standard for all clients.
Post-Migration Advice (From Our Experts)
For post-migration agility, you need validation, support, and automation.
Testing and Validation
The first step is validation, which ensures your new system works under real-world conditions.
- Chaos Engineering: Instead of just hoping the system works, apply chaos engineering principles by intentionally injecting failure scenarios (e.g., simulating a node crash) to validate that the new platform’s automated failover and self-healing mechanisms work as expected.
- Validation: Perform rigorous pre- and post-migration testing and thorough data validation, checking that all CDRs are accurate and all complex routing (IVRs, queues) functions correctly.
Shifting to a Proactive Support Model
Next, we need to answer what post-migration support is typically needed.
Well, support must shift from manual, reactive troubleshooting to automated, predictive management.
- Proactive NOC: Establish a Proactive Network Operations Center (NOC) model using Intelligent Automation (AIOps), predictive maintenance, and 24/7 monitoring to resolve issues before they impact the user experience.
- AI-Powered Triage: Leverage Remote Monitoring and Management (RMM) platforms, integrated with AI, to automate routine incident responses, freeing up expensive technician time for strategic tasks.
💡Our Experts Suggest
When migrating to a cloud-native ecosystem:
- Replace hardware security with API security.
- Audit every external endpoint (Webhooks, ESL connections) exposed by the new platform.
- Ensure you have governance processes and specialized tooling in place to spot “shadow APIs” and address configuration drift instantly.
This proactively manages the security risk that comes with increased application-level integration.
The transition from a fixed PBX to a cloud-native VoIP ecosystem is unavoidable.
For service providers, mastering the enterprise PBX migration solution blueprint is the difference between achieving sustainable growth and being bogged down by technical debt.
By standardizing the assessment, executing a phased, zero-downtime cutover using SRV records, and rigorously validating the resilience of the new architecture, you can eliminate technical debt and provide the foundation for sustainable growth. The payoff is substantial: lower operational costs, built-in disaster recovery, and the agility to integrate the next wave of AI automation instantly.
Ready for a scalable, cloud-native PBX? Get your custom migration roadmap!
Expert VoIP developers can smoothly enable this end-to-end transformation, moving you from legacy telephony to a scalable, resilient, and multi-tenant cloud ecosystem (in short: one ready for the future!).
Connect with experts to start!